Malware
Malware -- Its name comes from the words "malicious" and "software" and it represents virtually any digital threat. The premise that reunites all of the infections that fit in this category is that all of them cause a certain damage to the computer they've copied themselves to. Malware is the word used to define almost all of viruses available nowadays.
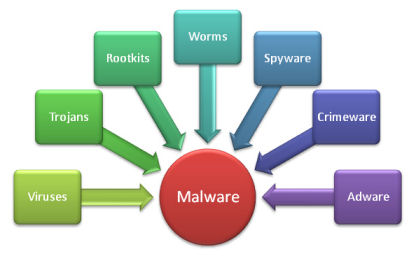
As a computer user, you're bound to come across terms such as "viruses," "adware," "trojans," and "spyware" – among many others. The internet is full of warnings about the latest Trojan horse barging its way onto user's PCs and bringing all of its malware buddies or that nasty virus causing tons of damage. Beyond knowing that the computer threats running amok can be anything from extremely irritating to downright devastating, do you know the difference between them?
Viruses
 The term computer virus is often used interchangeably with malware, though the two don't actually have the same meaning. In the strictest sense, a virus is a program that copies itself and infects a PC, spreading from one file to another, and then from one PC to another when the files are copied or shared.
The term computer virus is often used interchangeably with malware, though the two don't actually have the same meaning. In the strictest sense, a virus is a program that copies itself and infects a PC, spreading from one file to another, and then from one PC to another when the files are copied or shared.
Most viruses attach themselves to executable files, but some can target a master boot record, autorun scripts, MS Office macros, or even in some cases, arbitrary files. Many of these viruses are designed to render your PC completely inoperable, while others simply delete or corrupt your files—the general point is that a virus is designed to cause havoc and break stuff.
Damage is not always a side-effect of infection. Sometimes damage has been purposely built-in by the programmer. Some viruses are time activated; they silently spread for a number of days, months or years and will suddenly activate and do damage on one particular date. Other viruses are event driven. They will activate when something particular happens on a host, or when a command is sent to them via a covert Internet channel.
You can protect yourself from viruses by making certain your antivirus application is always updated with the latest definitions and avoiding suspicious looking files coming through email or otherwise. Pay special attention to the filename—if the file is supposed to be an mp3, and the name ends in .mp3.exe, you're dealing with a virus.
Trojans
 The purpose of a trojan is to conceal itself inside software that seems legitimate. The term ‘trojan’ is derived from the Trojan Horse story in Greek mythology, which explains how the Greeks were able to enter the fortified city of Troy by hiding their soldiers in a big wooden horse given to the Trojans as a gift. The Trojans were very fond of horses and trusted the gift blindly. In the night, the soldiers emerged and attacked the city from the inside.
The purpose of a trojan is to conceal itself inside software that seems legitimate. The term ‘trojan’ is derived from the Trojan Horse story in Greek mythology, which explains how the Greeks were able to enter the fortified city of Troy by hiding their soldiers in a big wooden horse given to the Trojans as a gift. The Trojans were very fond of horses and trusted the gift blindly. In the night, the soldiers emerged and attacked the city from the inside.
The disguises that a trojan can take are only limited by the programmer’s imagination. A common trick is to conceal the trojan inside a seemingly harmless game. Trojans also come disguised as videos, pictures and even legitimate software packages. In each case, the disguise is something designed to tempt into running it on his or her machine.
Cyber-crooks often use viruses, trojans and worms together. They design a trojan that "drops" a virus or worm onto the victim’s computer thus initiating a brand new infection. This virus or worm is usually called the "payload" of the trojan. Trojans also drop spyware.
Here are a few important reasons why you should never underestimate a Trojan horse:
• They might overtake the control of the computer
Probably, first and foremost is the reason that a hacker with the help of his sneaky little friend can easily take control of your computer – keyboard, mouse, printer, web cam, anything.
• Problems with FBI
We admit that the name might sound a bit too seriously but so can the problems be as your computer can be used to attack government sites, banks, etc. This is called DDOS attack. Its difference from other attacks is that this way a server is flooded with millions of entries at the same time causing it to overload and turn off. Even though, hackers do not have millions computers to perform these attacks, they may plant a Trojan in to your computer and use it to their advantage.
• Trojans may record your every keyboard click
Trojans are smart programs which makes them very hard to find. One of the most popular Trojan types is key-loggers. These Trojans record your every mouse click, every push of the keyword button. This way they get hold of your account details and then using your account, pretending to be you they send out links to malicious sites to your friends via a variety of social networks, Skype, email, etc.
• And last but not least, Trojans perform Man in the Browser operations
You probably have never heard of this before, but in some attacks against individuals, hackers do not even need full account details. They can plant a Trojan which will sit there quietly until you finish your online banking operation. Then, once you click confirm Trojan intercepts the transaction and redirects the money to the hackers' accounts. This is called Man in the Browser attack.
Rootkits
 One of the highly dangerous threats to your computer is Rootkits. Since it is invisible and attacks your computer from backdoors, it remains undetected for long and in the course causes you maximum harm. Rootkit and its consequences are not new to PC users; however, the capacity and reach of this malware has only increased with time, and more so in the recent years. Their secretive nature has been helpful to hackers, especially when it comes to infecting computers by placing malicious malware.
One of the highly dangerous threats to your computer is Rootkits. Since it is invisible and attacks your computer from backdoors, it remains undetected for long and in the course causes you maximum harm. Rootkit and its consequences are not new to PC users; however, the capacity and reach of this malware has only increased with time, and more so in the recent years. Their secretive nature has been helpful to hackers, especially when it comes to infecting computers by placing malicious malware.
Rootkit is dangerous software not because its attacks impose severe damages to a computer, but also because it embeds itself deep into the computer’s Operating System, making it harder to detect. It has been especially developed by hackers to gain unlimited access to a computer. Rootkits hides itself in system folders and slowly changes the registry settings to make it appear like an original file.
Rootkits have often been mistaken as a tool. However, in reality, it is not just a tool that exposes your PC to several risks rather it can be used as a gateway through which hackers can silently carry out the following tasks:
• Create backdoors that can be later used to gain access to a computer.
• Change the configuration settings.
• Hide logs that are left behind as a record of system intrusion.
In the above sense, Rootkits are dangerous because they are used by hackers to hide files, processes, folders or registry keys from getting detected at the scanning level by anti-malware programs. This sort of damage becomes almost impossible for a security scanner to repair, especially when the system has been infected.
Worms
 Worms are very similar to viruses in many ways. The biggest difference between a worm and a virus is that worms are network-aware. A virus finds it very easy to replicate itself amongst files on the same computer, however it has a hard time jumping from one computer to another. A worm overcomes this computer-to-computer hurdle by seeking new hosts on the network and attempting to infect them.
Worms are very similar to viruses in many ways. The biggest difference between a worm and a virus is that worms are network-aware. A virus finds it very easy to replicate itself amongst files on the same computer, however it has a hard time jumping from one computer to another. A worm overcomes this computer-to-computer hurdle by seeking new hosts on the network and attempting to infect them.
This is an important difference: in the past viruses could take years before moving from one corporation to another, or from one country to another. Worms are capable of going global in a matter of seconds. This makes it very hard for them to be controlled and stopped.
Spyware
 Read the first three letters of the name and you already know what it was built to do – "spy" on you and your activity on your computer.
Read the first three letters of the name and you already know what it was built to do – "spy" on you and your activity on your computer.
Spyware is any software installed on your PC that collects your information without your knowledge, and sends that information back to the creator so they can use your personal information in some nefarious way. This could include keylogging to learn your passwords, watching your searching habits, changing out your browser home and search pages, adding obnoxious browser toolbars, or just stealing your passwords and credit card numbers.
Spyware does not have any infection mechanisms. It is usually dropped by trojans (and also by viruses and worms). Once dropped, it installs itself on the victim's computer and sits there silently to avoid detection.
Unauthorized software installation without the owner/user's permission can include:
• Programs designed to steal personal user information to commit identity theft without
the user/owner providing permission.
• Disabling security
• Endless pop-up advertisements or adware.
• Modem Hijacking
• Changing browser settings
• Evading uninstalls by deceptive or unfair means
• Falsifying options for un-installation
• Installing personal and financial information collection features
• Installing keystroke logging software on a computer used or owned by someone whom
you are not responsible for their safety or conduct.
Since spyware is primarily meant to make money at your expense, it doesn't usually kill your PC — in fact, many people have spyware running without even realizing it, but generally those that have one spyware application installed also have a dozen more. Once you've got that many pieces of software spying on you, your PC is going to become slow.
Ransomware/Scareware
 Ransomware, otherwise called Scareware, is a malware program that will infect your computer and lock you out of it, demanding that you make a payment before it will unlock your computer. It may also ask you to complete a survey. Your computer can become infected with a Ransomware the same way it can become infected by a virus: if you open malicious email attachments, visit malicious or compromised websites, click on malicious links, or download software from untrusted sources.
Ransomware, otherwise called Scareware, is a malware program that will infect your computer and lock you out of it, demanding that you make a payment before it will unlock your computer. It may also ask you to complete a survey. Your computer can become infected with a Ransomware the same way it can become infected by a virus: if you open malicious email attachments, visit malicious or compromised websites, click on malicious links, or download software from untrusted sources.
Ransomware may also encrypt the files on your computer, making them unreadable, and demand a ransom in order to decrypt them; that is, making them readable again.
You should never pay the ransom these malicious programs demand that you do in order to have your computer unlocked or files decrypted. Sending your money to the cybercriminals behind these malicious programs will not guarantee that your computer will be unlocked or files decrypted.
Also, never send money or make any payments if you are instructed to do so via a message displayed on your computer screen. No law enforcement organizations like the FBI, CIA and others will lock your computer or encrypt your files, demanding a ransom or payment.
Adware
 Adware is a form of malware that serves up advertisements on the infected PC. It is commonly bundled up with free programs (like MSN messenger). Adware displays advertisements based on your individual preferences, such as: websites you've visited, buying choices, and the configuration of your computer's hardware and software. Adware has the capability to track your online activities, collect your web surfing habits, email addresses, and etc. It can also gather information about the hardware and software installed on your home computer and sends them to marketers.
Adware is a form of malware that serves up advertisements on the infected PC. It is commonly bundled up with free programs (like MSN messenger). Adware displays advertisements based on your individual preferences, such as: websites you've visited, buying choices, and the configuration of your computer's hardware and software. Adware has the capability to track your online activities, collect your web surfing habits, email addresses, and etc. It can also gather information about the hardware and software installed on your home computer and sends them to marketers.
Oftentimes, the internet user does not understand or read the usually long and confusing EULA (End User License Agreement) before agreeing to the terms because they are in a rush to download the free game, screen saver, utility or advertisement supported software. Advertisers typically do not consider adware as malware because the internet user agrees to the EULA before copying, downloading, installing, registering or using the software. The computer user should always read and make sure they fully understand the terms of the agreement before accepting. If you do not read and fully comprehend what you are agreeing to, you may be allowing a company or third party to monitor your activities online (where you go, where you shop, your web browsing history & preferences, and etc). So, make sure you read and understand all agreements before accepting them.
MALWARE INFECTIONS BY TYPE IN Q1 2013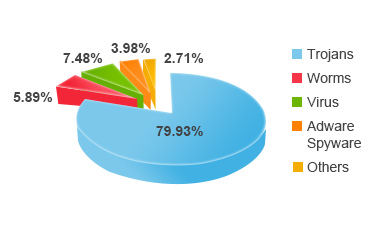
About
Call or email for consultation and appointment
Rampaul Enterprises
Tel: (800) 929-9291
Payment
I accept cash and Zelle for payment.
Copyright © 2013 to date. Rampaul Enterprises | All Rights Reserved

